ProcessUnity for Cybersecurity Risk Management
Accelerate SOC 2 Certification
Accelerate SOC 2 audit preparation with automated control mapping, tools for evidence collection and real-time reporting available with ProcessUnity for Cybersecurity Risk Management.
SOC 2 certification highlights your security program’s progress, earns trust from clients and builds competitive advantage. Though preparing your cybersecurity program for a SOC 2 audit can be challenging, partnering with the right technology and expertise will make it easier to accelerate.
ProcessUnity for Cybersecurity Risk Management assists your team in organizing controls, policies and evidence for SOC 2 audit. The platform leverages a pre-mapped control framework to provide visibility into alignment with your trust service criteria (TSC), giving you the insight to improve your security posture.
Key Benefits:
- Map existing policies, procedures and controls to selected trust service criteria
- Baseline and improve control effectiveness
- Centralize documentation for audit
- Automate third-party risk assessments
- Create tailored reports to prepare for audit
ProcessUnity can help your organization accelerate SOC 2 certification more efficiently with tools to:
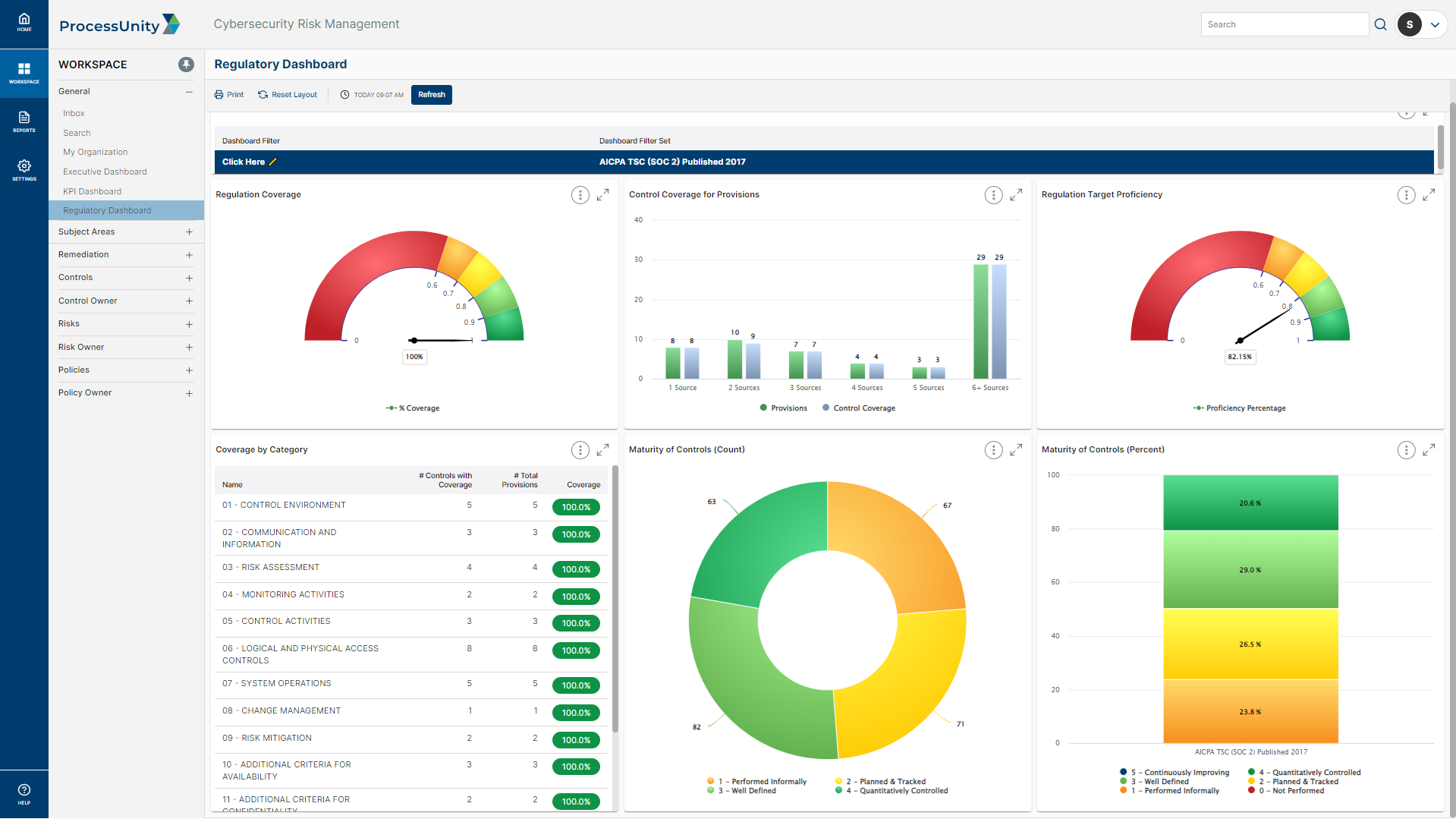
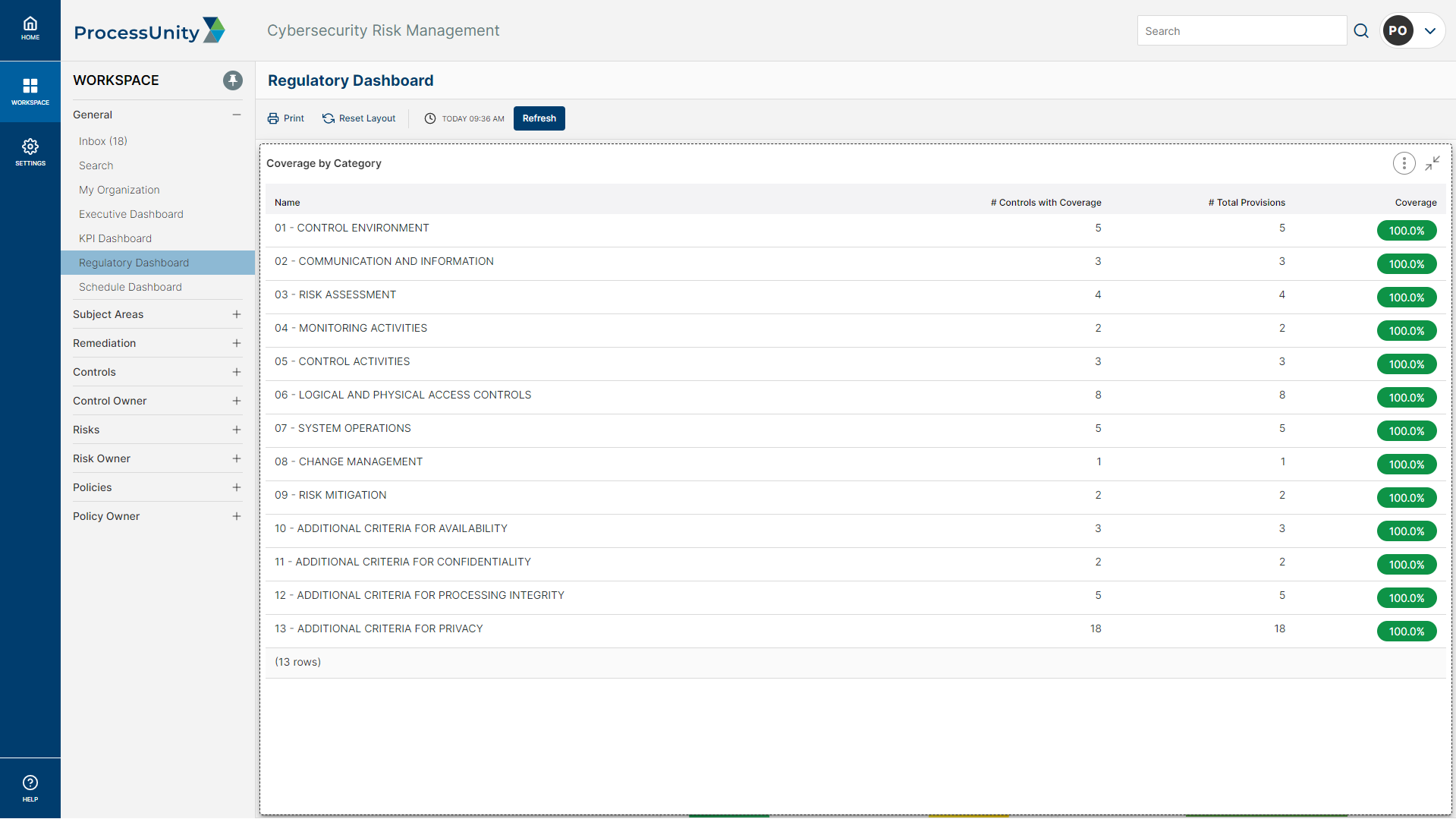
Map Internal Policies and Procedures to SOC 2 Domains
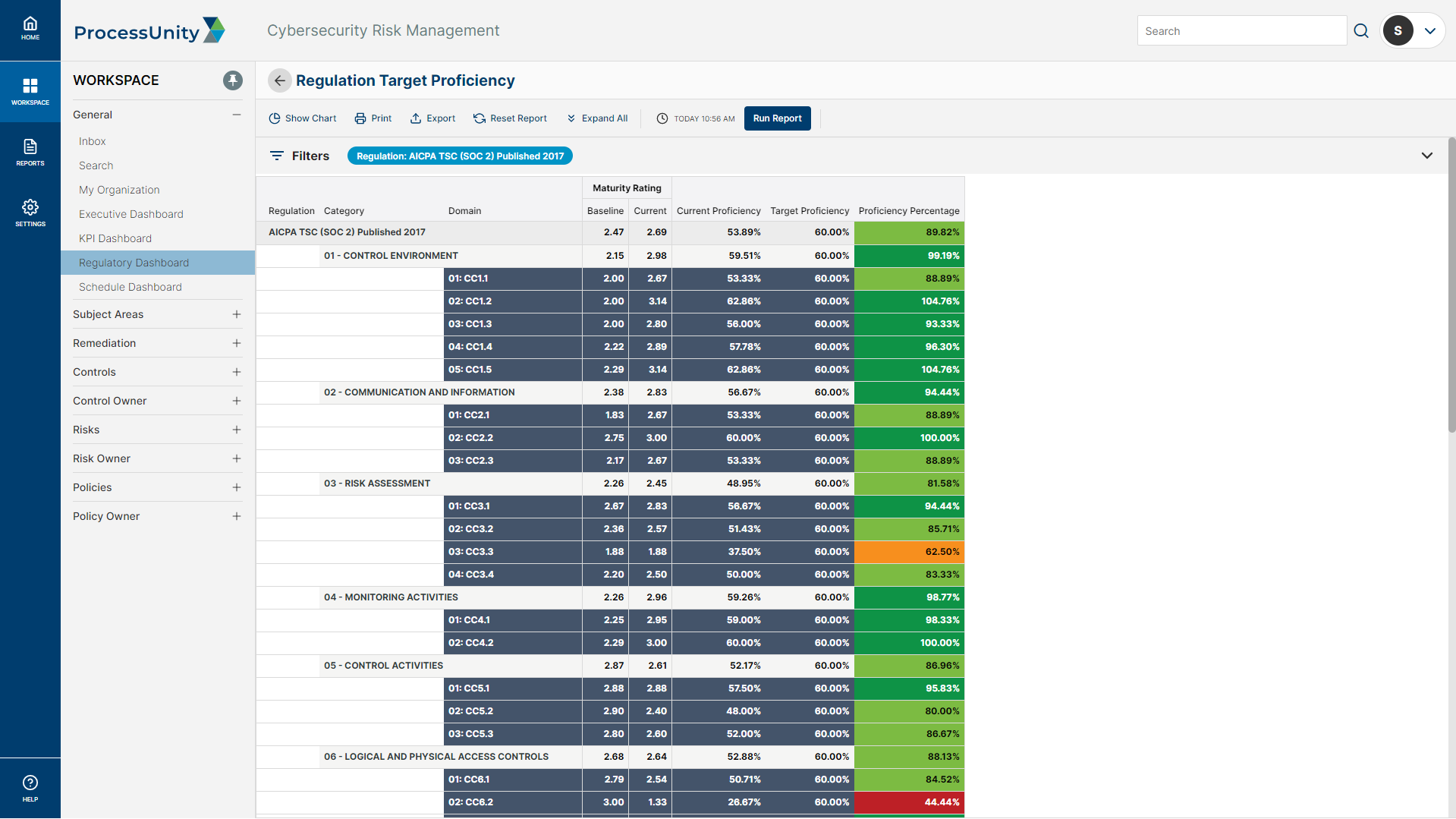
To avoid duplicative work, your team must identify and map your existing policies and procedures to your SOC 2 trust service criteria. Manually mapping this information is labor intensive, often requiring the help of a consultant. ProcessUnity provides a pre-mapped control framework that can be mapped to your policies and procedures, identifying gaps in your control structure and revealing where to add or update controls.
Baseline and Assess Control Effectiveness
SOC 2 helps baseline your control effectiveness and then progress towards set targets. The ProcessUnity Control Assessment Engine automates control reviews, ensuring you get on-time information to baseline and monitor control effectiveness. The platform triggers assessment distribution to assigned stakeholders based on your cadence, keeping control assessments on track throughout the year.
Gather Evidence of Control Effectiveness
When you need control evidence for an audit, you don’t want to rely on the timeliness of other stakeholders. ProcessUnity helps you get on-time information with escalation reminders and notifications to control and asset owners. The platform centralizes evidence collection in a single database, allowing you to organize and access evidence for audit.
Automate Third-Party Risk Management
SOC 2 requires organizations to demonstrate robust internal and external security practices, meaning you must continuously monitor third-party risk. ProcessUnity includes workflows for assessing third-party risk and factoring external control effectiveness into your overall control rating. Third parties can be monitored by criticality, allowing you to prioritize external issue remediation based on relevant risks to your business.
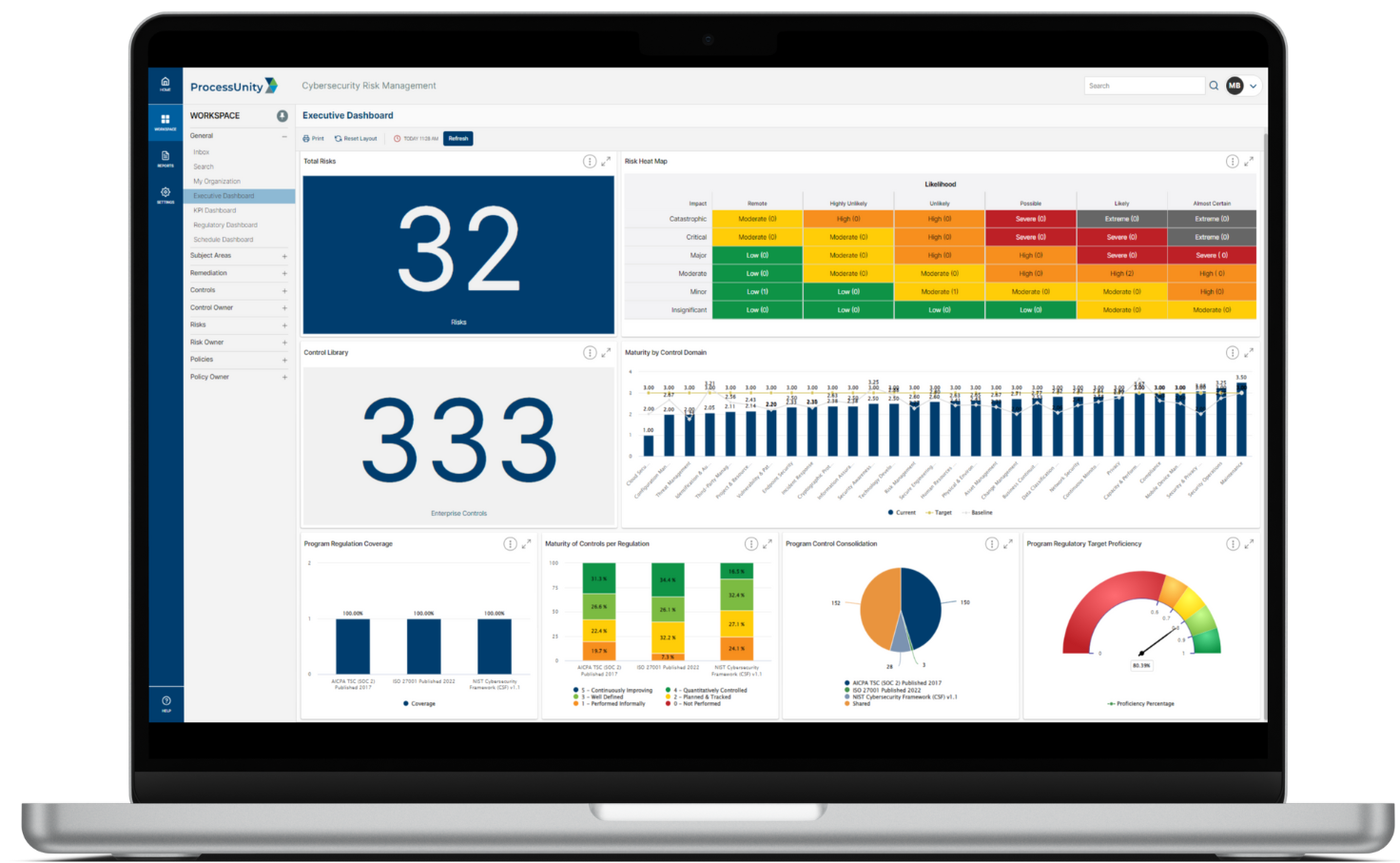
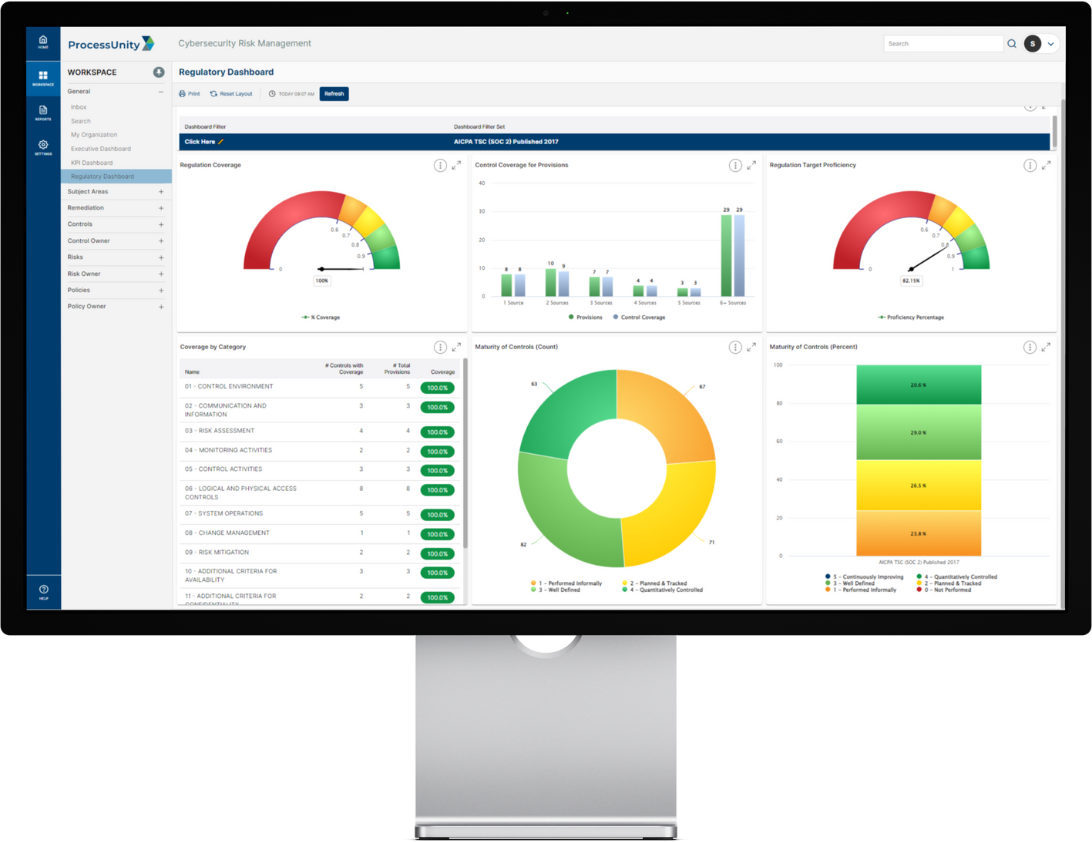
Report on Controls and Risks in Real Time
Auditors look for easy-to-read, comprehensive reports that detail your program’s commitment to continuous improvement. ProcessUnity helps you generate reports in seconds, reducing the time it takes to gather program data and report on findings. For your team, real-time reporting provides complete visibility into your program, helping you stay on top of issues and continuously improve your security posture.
Continuously Improve Cybersecurity Controls
Maintaining your SOC 2 certification as your business grows means continuously improving your security posture. ProcessUnity provides real-time monitoring of cybersecurity controls, risks and compliance, enabling your team to identify and address issues quickly. Reporting tools allow you to benchmark your program and measure performance against targets, providing visibility into where to allocate remediation efforts.
Accelerate SOC 2 Certification with ProcessUnity Cybersecurity Risk Management
ProcessUnity helps organizations of all sizes prepare for a SOC 2 audit more efficiently with out-of-the-box control mappings, automated evidence collection, third-party risk management workflows and real-time reporting.
Contact us here to talk with one of our SOC 2 experts about ProcessUnity for Cybersecurity Risk Management.
Request a Demo: ProcessUnity's Cybersecurity Risk Management Platform
Hundreds of organizations worldwide rely on ProcessUnity Cybersecurity Risk Management to implement a centralized system of record for managing cybersecurity activities across the organization. Contact us to start your journey today!
Request a Demo: ProcessUnity's Cybersecurity Risk Management Platform