Featured Resources
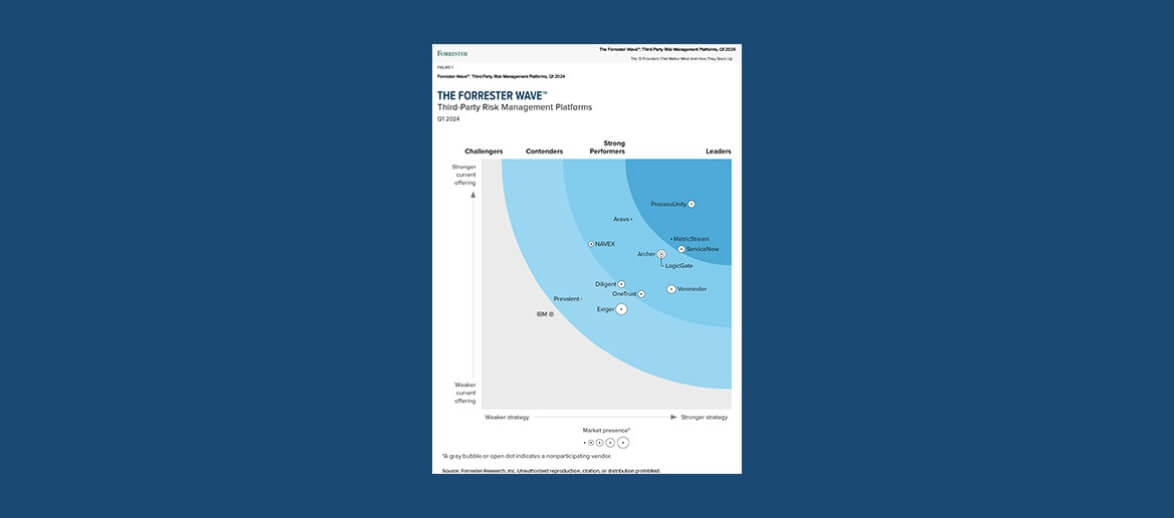
ProcessUnity is a Leader in The Forrester Wave™: Third-Party Risk Management Platforms
Content Library
Announcing the ProcessUnity Trust Center: Transparency You Can Rely On
When it comes to meeting risk and compliance standards for your business, trust is the constant end goal. Your customers, partners, regulators, and board of directors all want the same thing: clear and current evidence that the companies you work with take security and compliance seriously. That’s why we created the ProcessUnity Trust Center, a […]
Introducing Assessment Autofill: Transforming How Third-Party Security Teams Complete Risk Assessments
If you’re part of a client security assurance team, you know the feeling all too well: the never-ending stream of due diligence requests, the stack of security questionnaires, and the tedious process of copying answers from one spreadsheet into another. What should be a simple opportunity to demonstrate your organization’s security posture often becomes a […]
Manual vs Automated Vendor Risk Assessment: A Modern Guide to TPRM
Every third-party relationship is an entry point for risk. With the average enterprise managing hundreds, if not thousands, of third parties, that’s a lot of entry points. Yet, 50% of organizations still rely on spreadsheets to assess their vendors. Manual processes can’t keep up with today’s pace of business. Traditional risk management methods slow onboarding, […]
Why AI Alone Isn’t Enough: The Case for Workflow-Driven, Data-Focused Third-Party Risk Assessments
Artificial Intelligence (AI) is currently the headline act in third-party risk management (TPRM). From auto-answering questionnaires to reviewing evidence, AI accelerates efficiency and eliminates manual busywork. But here’s the truth: AI is only as effective as the program workflow that guides it. When managing assessments in the TPRM space, you need more than an algorithm. […]
Summary: Delivering Value Via ProcessUnity's Global Risk Exchange
As modern business ecosystems grow more interconnected, managing third-party risk is more critical — and complex — than ever. Manual assessments can’t keep up, delaying onboarding, draining resources, and creating blind spots in risk visibility. ProcessUnity’s Global Risk Exchange offers a faster, smarter approach. Gain access to the world’s largest library of third-party data — […]
From Long Hours to Instant Insights: The Case for Automating Third-Party Evidence Review
Third-party risk teams face a growing challenge. As the volume and complexity of third-party assessments increases, so does the burden of reviewing evidence. Documents such as SOC 2 reports, SIG questionnaires, and internal security policies must be analyzed in detail before a third party can pass a yearly review cycle. While these documents are critical […]