Safeguard Your Brand from Emerging Threats in Your Third-Party Ecosystem
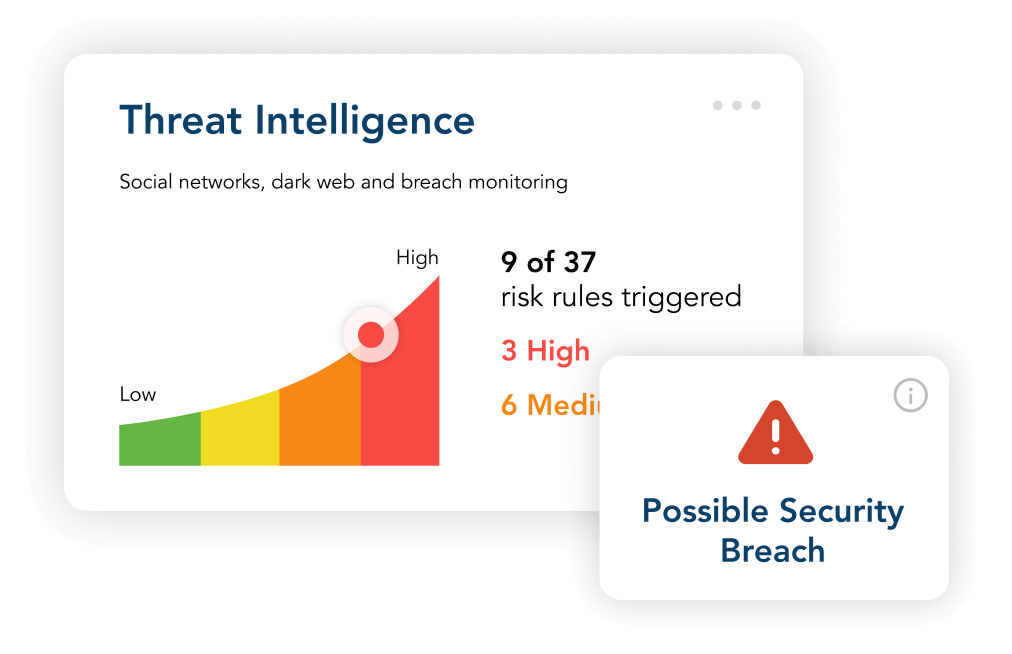
It’s not enough to solely focus on protecting your internal systems and applications from emerging threats and potentially exploitable vulnerabilities – any disruption or incident that occurs within your portfolio of third parties, vendors, and suppliers could have just as big of an impact on your business operations and brand. With the sheer volume of vulnerability alerts topping 30,000 annually, it’s nearly impossible to keep tabs on them all, let alone assess all your third parties each time something new arises.
A New Way to Manage Cyber Threats & Known Vulnerabilities
ProcessUnity Threat & Vulnerability Response is an all-in-one solution for third-party risk management and information security professionals that:
- Monitors advisory sources for critical vulnerabilities
- Determines which of your third parties should be assessed for each vulnerability
- Bulk assesses potentially affected third parties
- Generates management reports to communicate findings and recommendations
With Threat & Vulnerability Response, your team can reduce the emergency assessment process from weeks or months down to a few short days.

Whitepaper
TPRM: Tracking & Mitigating Emerging Threats
ROI Calculator
Calculate Your ROI and Generate Savings Report
From Threat Alerts to Action: Mitigate Vendor Risks Effectively
Monitor Vulnerability Alerts
Threat & Vulnerability Response from ProcessUnity integrates advisories from NIST’s National Vulnerability Database and CISA’s Known Exploited Vulnerabilities, and automatically alerts your team when high-risk exposures have been identified. Based on the severity, ProcessUnity kicks off workflows to initiate the vendor assessment process without direct effort needed from your team.
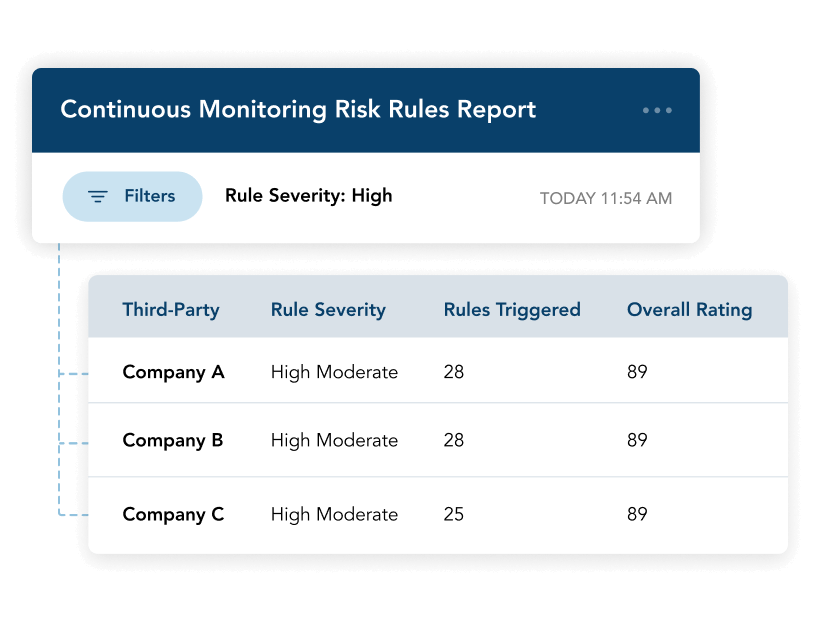
Prioritize Which Third Parties Should Be Assessed
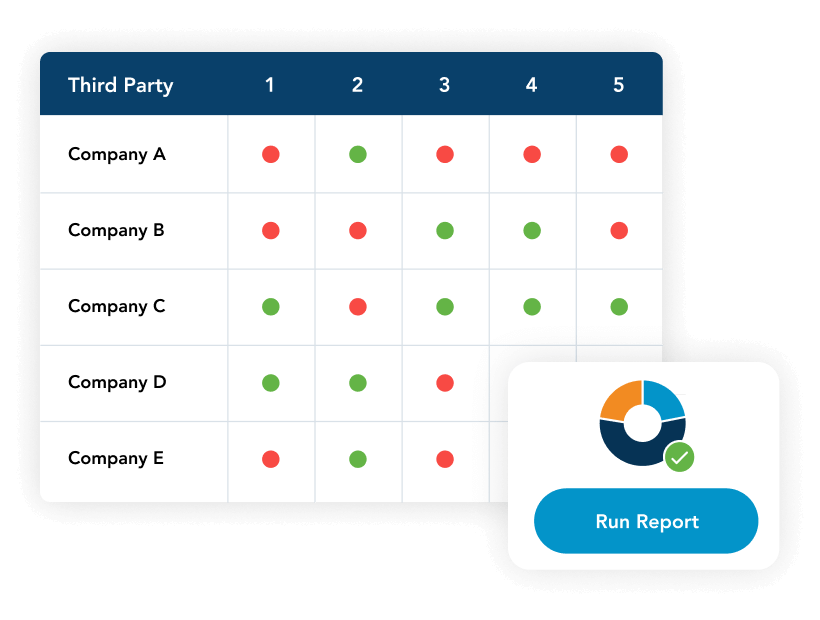
ProcessUnity helps you narrow your assessment focus, so your team doesn’t waste time evaluating service providers unnecessarily. Using a combination of inherent risk, geographic, firmographic, and technographic information, Threat & Vulnerability Response determines which of your vendors are most critical to your business operations and are using the compromised technology.
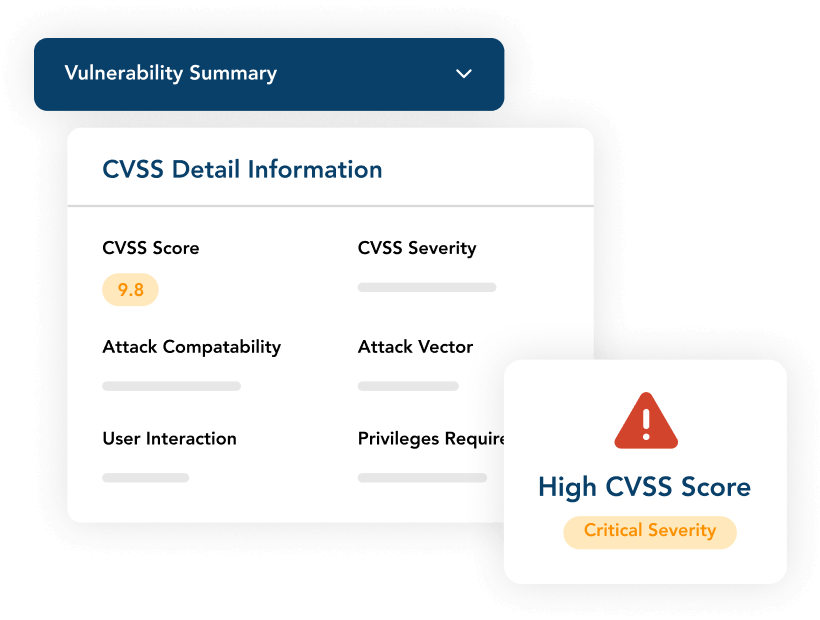
Initiate Emergency Assessments, Score the Results
ProcessUnity immediately creates and distributes threat-specific assessments to the appropriate third parties. Your third parties complete the assessment via our secure online portal. The platform then automatically scores answers based on a set of preferred responses to quickly narrow your team’s attention where it’s needed. One-click reporting generates an executive summary of the threat, the impacted third parties, and the actions taken.
Our Platform Solutions
Identify when threats and vulnerabilities emerge and quickly gauge your third party ecosystem for susceptibility via a four-step vendor prioritization and assessment process. Reduce your response time from weeks or months to a few short days.
Learn MoreAutomate the complete third-party risk lifecycle, from initial onboarding to ongoing monitoring, with the industry’s most configurable workflow platform.
Learn MoreAccess the industry’s most extensive network of pre-validated vendor assessments and real-time risk intelligence. Our exchange platform enables organizations to make faster, more informed decisions using shared risk data, eliminating redundant assessments and providing deeper insights into potential vulnerabilities across your vendor ecosystem.
Learn More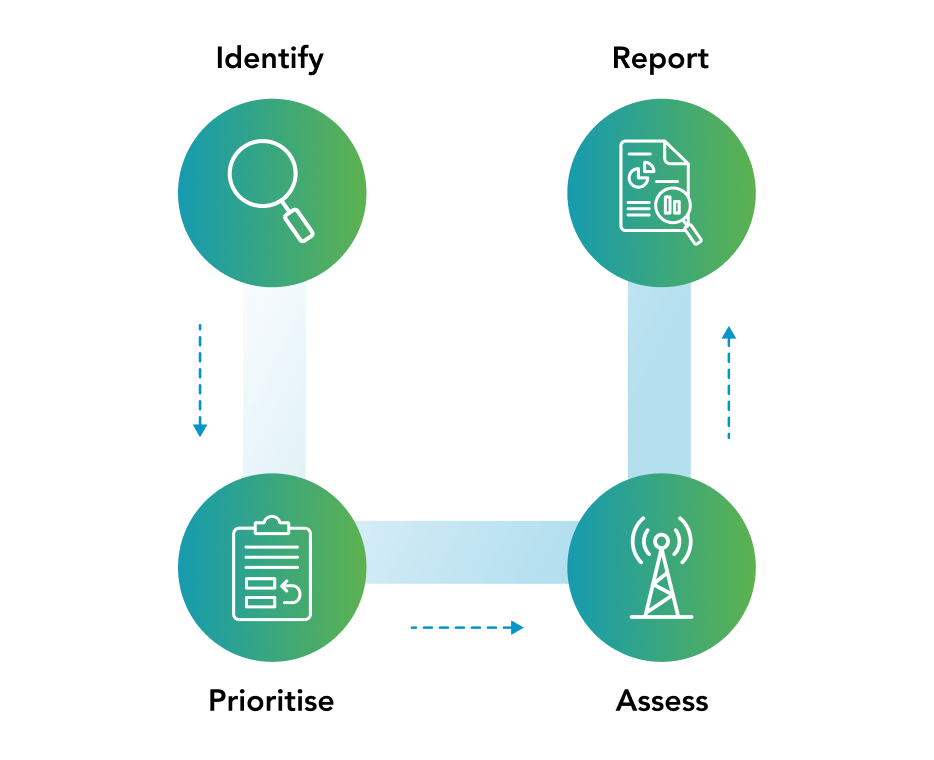
Next Steps:
Schedule a ProcessUnity Platform Demo
Our team is here to show you how forward-thinking organizations are elevating
their
Third-Party Risk Management programs and practices to maximize risk
reduction. Start
your journey with ProcessUnity today.